Cybersecurity threats continue to be in a constant state of change and evolution as attackers discover new ways to compromise information and data, both at corporate and personal levels. In fact, the FBI’s Internet Crime Report from 2022 revealed that there are approximately 3.4 billion spam and phishing emails sent daily and that phishing is responsible for 90% of data breaches. The global average data breach cost was $4.35 million in 2022.
At SitelogIQ, we’re committed to educating our employees and customers on cybersecurity best practices as well as raising awareness about potential cyber threats to keep on their radar. Cybersecurity Awareness Month is a great time to review those tips and continue to educate ourselves to ensure we safeguard our sensitive information.
Cybersecurity Threats to Keep on Your Radar
Cybersecurity incidents continue to increase in frequency and severity and often require additional countermeasures or damage control to protect data and personal information. Of those incidents, the most common are phishing emails and social engineering. Phishing emails use deceptive emails, messages, ads, or sites that look similar to those you already regularly use and interact with in an attempt to steal your sensitive information. Social engineering attacks involve an attacker using human interaction and social skills to obtain or compromise an organization’s data or its computer systems. The most common social engineering threats come in the form of digital, in-person, and mobile/phone attacks.
The good news is there are a few key indicators that can help you identify and avoid these common cybersecurity threats. Be on the lookout for these red flags:
- “Urgent, do this now!” The bad guys typically create a sense of urgency to get you to click a link or open an attachment.
- Email addresses that closely resemble one from a reputable company by altering or omitting a few characters, for example, JDoe@gooogle.com or John.Smith@apple-support.in. The branding of the email can look legitimate but the email address identifies it as a scam.
- Spoofed hyperlinks and Websites are made to look legitimate, but the URL may vary by spelling or site domain.
- Poor grammar and sentence structure, misspellings, and inconsistent formatting throughout the message.
Our Top Cybersecurity Tips
In addition to the red flags listed above, there are a few cybersecurity best practices you can implement every day to help protect yourself online.
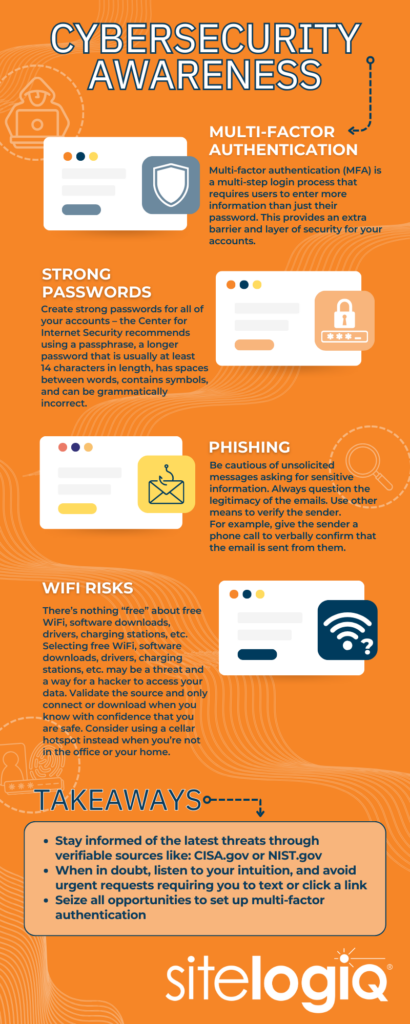
Multi-factor authentication (MFA) is a multi-step login process that requires users to enter more information than just their password. This provides an extra barrier and layer of security for your accounts. Since implementing an MFA solution our account breaches have significantly reduced.
- Multi-factor authentication (MFA) is a multi-step login process that requires users to enter more information than just their password. This provides an extra barrier and layer of security for your accounts. Since implementing an MFA solution our account breaches have significantly reduced.
- Create strong passwords for all of your accounts – the Center for Internet Security recommends using a passphrase, a longer password that is usually at least 14 characters in length, has spaces between words, contains symbols, and can be grammatically incorrect. These are often best if the words are completely random, which can be easy to remember but makes it harder for hackers to crack. You can use a random combination of words to form a passphrase or a keyboard pattern passphrase like “Quick Warm Earth Random Toboggan”. You can also use the first or last letter of words in a sentence to create your strong password. For example, “My first automobile was a black Ford pickup truck made in Detroit Michigan!” would translate to “MfawabFptm@DM!”.
- There’s nothing “free” about free WiFi, software downloads, drivers, charging stations, etc. Selecting these free options may be a threat and a way for a hacker to access your data. Validate the source and only connect or download when you know with confidence that you are safe. Consider using a cellar hotspot instead when you’re not in the office or your home.
- Before signing up for online services on your work device, check with your Information Technology team to ensure its security.
While Cybersecurity Awareness Month is a great time to refresh yourself with best practices, it’s critical to incorporate these best practices into your every day habits when receiving, engaging, and responding to any message – both professionally and personally. Keeping these tips and tricks in mind will help you protect your personal information and that of your organization.